Should passwords be phased out?
That was the question asked by a panel at the White House Summit on Cybersecurity and Consumer Protection held Friday at Stanford University.
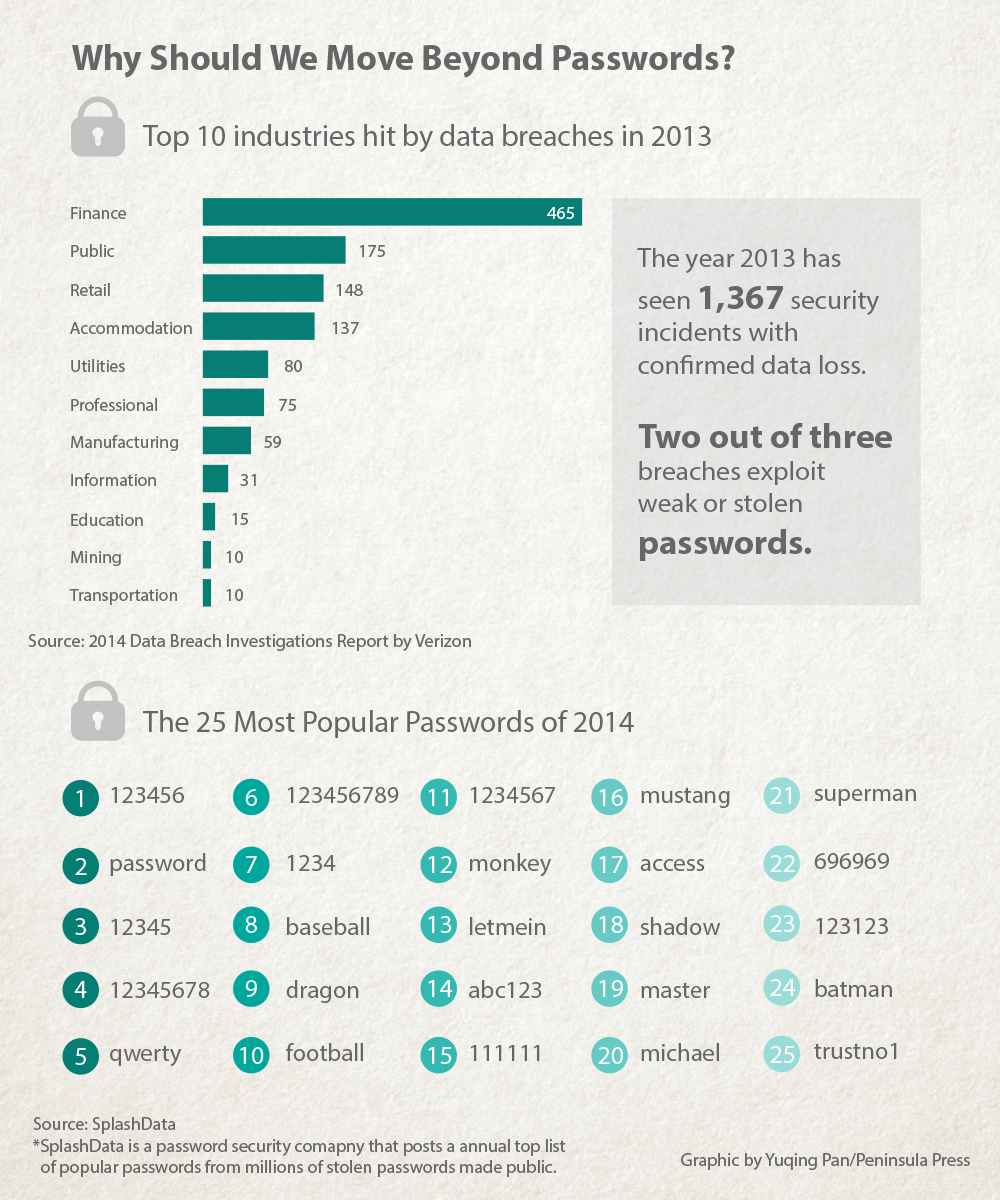
Given that two out of three security breaches exploit weak or stolen passwords, according to a Verizon 2014 Data Breach Investigations Report, and that more than 13 million Americans were victims of identity theft-related fraud in 2013, according to another report by the Consumer Federation of America, password management is one of the biggest cybersecurity concerns.
“ID fraud is not going away, it’s only getting worse. There’s no silver bullet. And passwords on their own are not 100 percent effective,” LexisNexis Chief Executive Officer Mark Kelsey said Friday.
That is certainly not helped by the fact that the most popular passwords in 2014 were still “123456”, “password” and “12345”, according to SplashData, Inc. a password security company, which compiled millions of stolen passwords made public last year.
Even if people do create longer and more secure passwords, the problem is – they are more likely to forget them. Password refreshing can be time-consuming and costly, said Kelsey.
Asking people to change their password frequently doesn’t help either. In fact, it hurts security because when people have to change their passwords, they choose weaker and weaker passwords, said Lorrie Faith Cranor, a professor of computer science, engineering and public policy at Carnegie Mellon University.
So what’s the solution? One possibility is multi-factor authentication, a system that employs multiple security steps, such as something you know (your password) and something you have (your phone). The two-step verification is widely used by Google, Dropbox, Twitter and Facebook. Apple has recently added two-step authentication to iMessage and FaceTime.
“We owe them (consumers) nothing less than the best protections that we can possibly provide by harnessing the technology at our disposal. We must get this right,” Apple Chief Executive Officer Tim Cook said at the summit.
Another step, recently taken by the U.S. Automobile Association includes facial and voice recognition. The association is trying out that technology on its mobile app to bolster PIN protection. Users can log in with a tap of their smartphone camera and a blink when prompted (to prove they’re a live person and not a photo). They can also log in by speaking into the phone.
While businesses are pushing for more security measures, consumers are too.
“Consumers who are coming to us and say, ‘I want to take control of my own identity, I don’t trust the government, I don’t trust Google,’” said Stina Ehrensvard, CEO and founder of identity protection company Yubico, an international identity protection company based both in Palo Alto and Sweden.
Yubico launched its product – the Yubikey – last year. Yubikey is a USB stick that can be plugged in a computer or a smartphone to ensure a secure online login. In addition to typing in the password, the user can tap on Yubikey to generate a code – which changes with every login –and authenticates the user.

At the same time companies are attempting to make identity more secure, some are trying to make identity management simpler.
Virginia-based ID.me is an identity verification network that allows users to prove their group affiliations – such as military, teacher, student – online. They can then use this “portable” credential across different online platforms. For example, a veteran can use his troop ID to create a portable ID so that he can use it to get a veteran’s discount at an online retailer or access his medical records in a Department of Veterans Affairs hospital.
“We don’t believe that consumers should have to create a new account every time he visits a website, we believe they should be able to use trusted credentials,” said Blake Hall, CEO of ID.me.
“I don’t think we are going to get rid of the password anytime soon, as much as we’d like to,” added Carnegie Mellon’s Cranor. “In the short term, we are going to augment them.”
The transition to new forms of password protection won’t necessarily be an easy one. Steve Emmert, senior director of government and industry affairs at Reed Elsevier Inc., an attendee of the cybersecurity summit, raised question about the use of biometrics.
The use of facial recognition or fingerprints is not protected by the Fifth Amendment against self-incrimination, Emmert said. A Virginia court last year ruled that police officers can force criminal suspects to unlock their phones with a fingerprint scanner, even though they cannot force them to divulge cell phone passwords.
“It is going to dramatically undermine biometrics if users can be forced to give up access of their devices, with more and more data on those devices,” said Emmert.
Another issue facing password management is its use across different devices. Users find it frustrating to generate a complicated password on a laptop, only to find it painful to type it on tablets, let alone a wearable device.
“Some of the solutions are getting us there, but from a usability perspective, I’m not sure there’s a ‘one there’ yet,” said Cranor.
CORRECTION – Editor’s Note (2/18/2015): In this story originally published Feb. 14, 2015, Peninsula Press had a transcription error in LexisNexis Chief Executive Officer Mark Kelsey’s first quotation. The corrected quote appears in the story above.
